Financial crime is both pervasive and rapidly-evolving in nature and has compelled financial institutions to push the innovation envelope with regard to data, analytics, machine learning, and AI technologies.
This story is the third in a series about moving towards the next gen financial crimes platform. In my previous stories, I describe how we respond to the “The Pervasiveness Of Financial Crime” within the context of the “New Approaches To Combating Financial Crime” that are evolving in the financial services industry.
The Limits of Traditional Financial Crimes Platforms
Traditional financial crime platforms have a limiting effect on our capabilities to combat financial crime. The narrow specialization that each platform has towards a specific crime type makes it hard to see the big picture. For example, money laundering is a mechanism by which to “cash out” of underlying crimes like cybercrime, fraud, human trafficking, and drug smuggling. It is also a mechanism by which to finance bribery, corruption, and terrorism. Focusing only on AML is just a portion of the larger problem. An understanding of the big picture is needed because financial crime is pervasive, interconnected, and ever-evolving.
Other limitations of traditional platforms are the age of the technology employed and the cost and complexity of retrofitting those platforms to counter new crime patterns. As a result, we’ve developed a myopic view that focuses on reverse engineering binary transactions between parties after-the-fact (even for events that were initially detected in real-time).
The problem is that we are behind the times. Criminal networks are on the cutting edge of technology, so crime patterns that worked ten years ago (or even six months ago) are no longer in play. They’ve moved on to something else.
Resolve Limitations
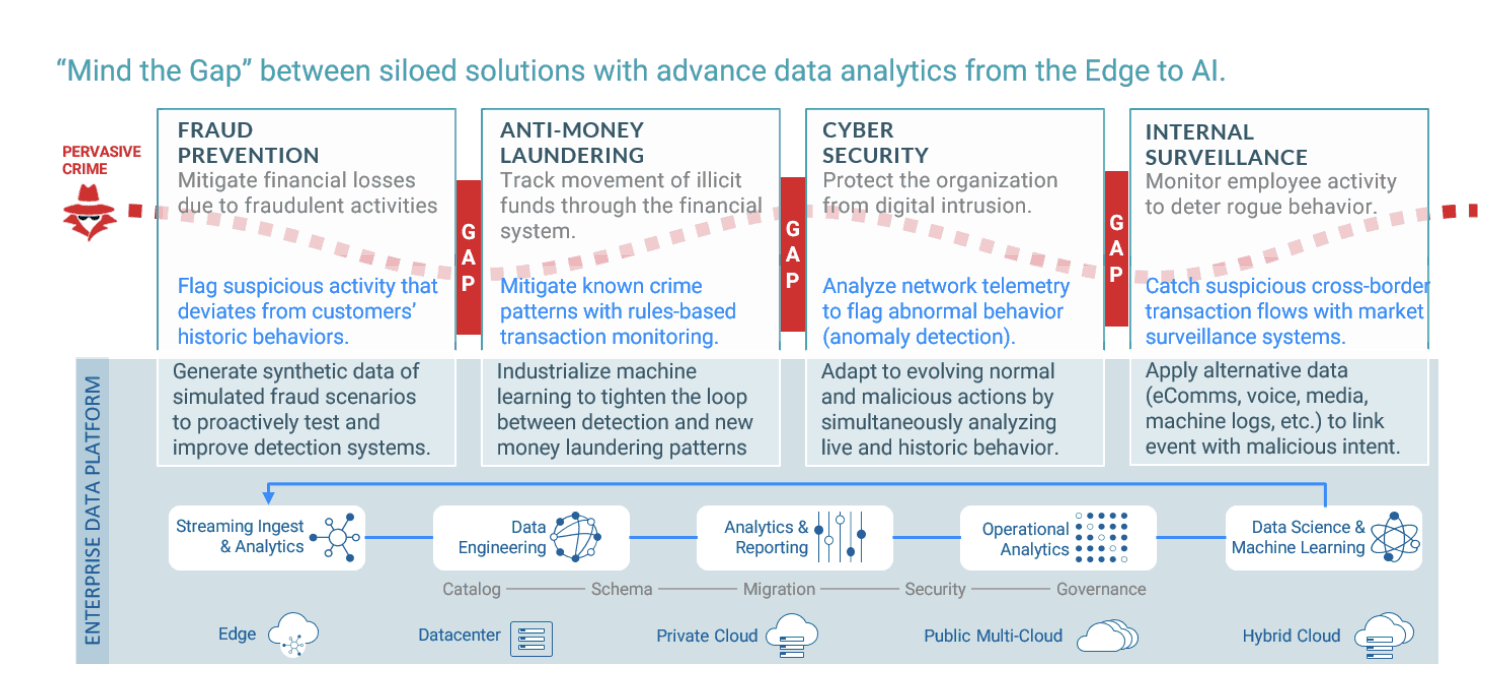
The diagram below sets the stage for where the limitations occur and how they might be resolved. It illustrates how traditional financial crime platforms create silos of specialization (fraud, anti-money laundering, cybersecurity, and internal surveillance). An example of a standard solution is provided for each.
These siloed business functions are problematic for two reasons.
- Opportunities are provided for criminals to sneak into the financial system and spread rapidly; and
- Intelligence gaps keep us from stitching together events and behaviors that could disrupt criminal networks.
The blue base at the bottom represents what is needed, an enterprise data platform that enables converged and integrated data and analytics functions with the ability to develop and deploy data science and machine learning projects across the enterprise. This enables the organization to:
- Enrich solutions per crime specialization (examples provided in the diagram); and
- Remove the gaps in-between each of the silos.
Moving Forward
The Enterprise Data Platform represents the next-gen financial crimes platform. Below I expand on this concept by presenting what we need to do in order to proactively disrupt criminal networks today and anticipate the challenges ahead.
Our engagement needs to be more holistic: We work best in structured environments that have clear boundaries of business functions, methods, and technologies (silos). To be effective, we should continue this because it enables us to leverage our subject matter expertise. But we need to reduce the resulting intelligence gaps that criminals are able to exploit.
Two considerations that are critical for the next-gen solution include:
- Deploying an enterprise-wide data platform to unify disparate data sources and data management processes and reduce the siloed divisions between business, risk, and crime teams, enabling better collaboration.
- Enable machine learning models to be developed and tested natively and deployed to endpoints so that detection and prevention is dynamic and enterprise-wide.
Our actions need to be more current: We come to understand criminal activity after the fact by reverse engineering events, even those that were initially captured in real-time. This helps to establish an evidence trail to support enforcement actions but they are often brought against schemes that go back years. Deterministic rules-based solutions create a dependency on historic data that flag old types of illicit activity and these rules are difficult to quickly revise in order to keep current.
To this end, a next-gen solution leverages advanced mechanisms such as:
- Industrialized machine learning to tighten the loop between detection of and responding to new fraud patterns.
- Fraud simulation to test in-house and third-party solutions against increasingly complex scenarios of criminal behavior that is not dependent on historical data and past observations.
We need to better understand behaviors and relationships: Criminals and the people/institutions that they victimize behave differently. Without understanding behavior, we only identify the actions of criminal networks, not the networks themselves and the people they victimize. Add in another twist. Synthetic identity fraud is the fastest-growing type of financial crime in the United States. Real people and fake people can make similar transactions but their social behaviors won’t match because, well, the latter aren’t people (big, big difference).
A next-gen financial crimes solution would facilitate the following:
- Enhance machine learning models at the edges of the financial network (ATMs, Points of Sale (PoS), digital and wearable devices, etc.) with algorithms that have been built and back-tested on petabytes of data managed in the enterprise data platform. By extracting model features and aggregations over time from high throughput streaming data, you will be able to generate a profile describing the behavior of an entity.
- Leverage alternative data sources that go past credit history, bank transactions, and personal identifiers to help distinguish real people from fake ones. Third-party data sources allow banks to deepen their understanding of their customers and develop holistic KYC. Real people have a depth of experience that results in behaviors that aren’t readily replicated by synthetic identities (i.e. a social / internet history that is not the age of an infant).
We need to keep up with the latest technologies: The threat horizon is borderless because there are no boundaries between the physical world (people and things), the virtual world (electronic banking), and ever-new points of entry (wearable and device-based contactless payments). There are so many options available for criminals to develop their next big heist. Keeping up is expensive because it is cumbersome to update the array of systems and infrastructure on the fly, especially as it relates to AI.
A next-gen financial crimes solution would:
- Support and encourage the latest open source advances to ensure the adoption of the latest technologies and algorithms.
- Enhance existing financial crime detection systems by plugging them into a common data experience and leverage the data results from open-source advances described above.
We need to reduce false positives: Financial crime units are inundated with alerts that incorrectly indicate something bad is going on. These are called false positives and they are costly because they require staffing resources to handle the overload and they also impact customer service. A false fraud alert could freeze a credit card and if that happens often, customers can get frustrated and move to a competitor.
As a whole, this is what the next-gen solution is for. False positives are due to our limited view of what is going on. If our engagement is holistic, our actions are current, and we understand behaviors and relationships with the help of the latest technologies, the rate of false positives can go down because we are better informed.
What the Next-Gen Platform Looks Like
The diagram below provides an example of the next-gen financial crimes platform, using the Cloudera Data Platform as an example.
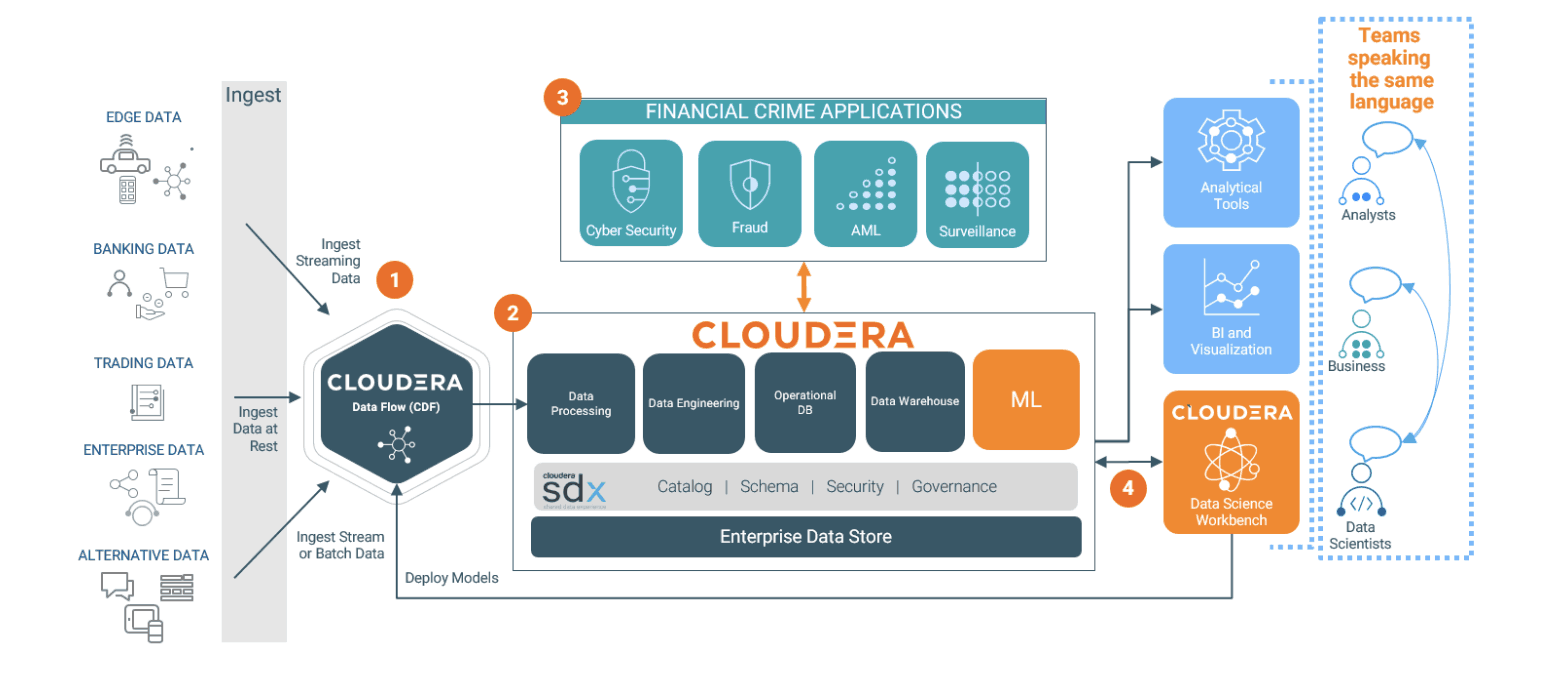
- Any type of data (streaming from the edge, batch, structured, and unstructured) can be ingested and processed in real-time using Cloudera DataFlow (CDF).
- The Cloudera Data Hub provides a shared, scalable, data store with built-in security, governance, and compliance that can be used by third-party platforms, analysts, data scientists, and businesses.
- Financial services organizations can run their existing best-of-breed financial crime solutions and applications on Cloudera while leveraging petabytes of high-fidelity data across organizational boundaries.
- Machine learning models are developed and tested natively and deployed back to the edge using Cloudera Data Science Workbench.
The Foundation of a Next-Gen Platform
Next, I will describe the foundation that pulls the technologies highlighted above into a comprehensive solution to the industry-wide challenges of combating financial crime. I will also be covering this and specific customer examples on our upcoming webinar as well.
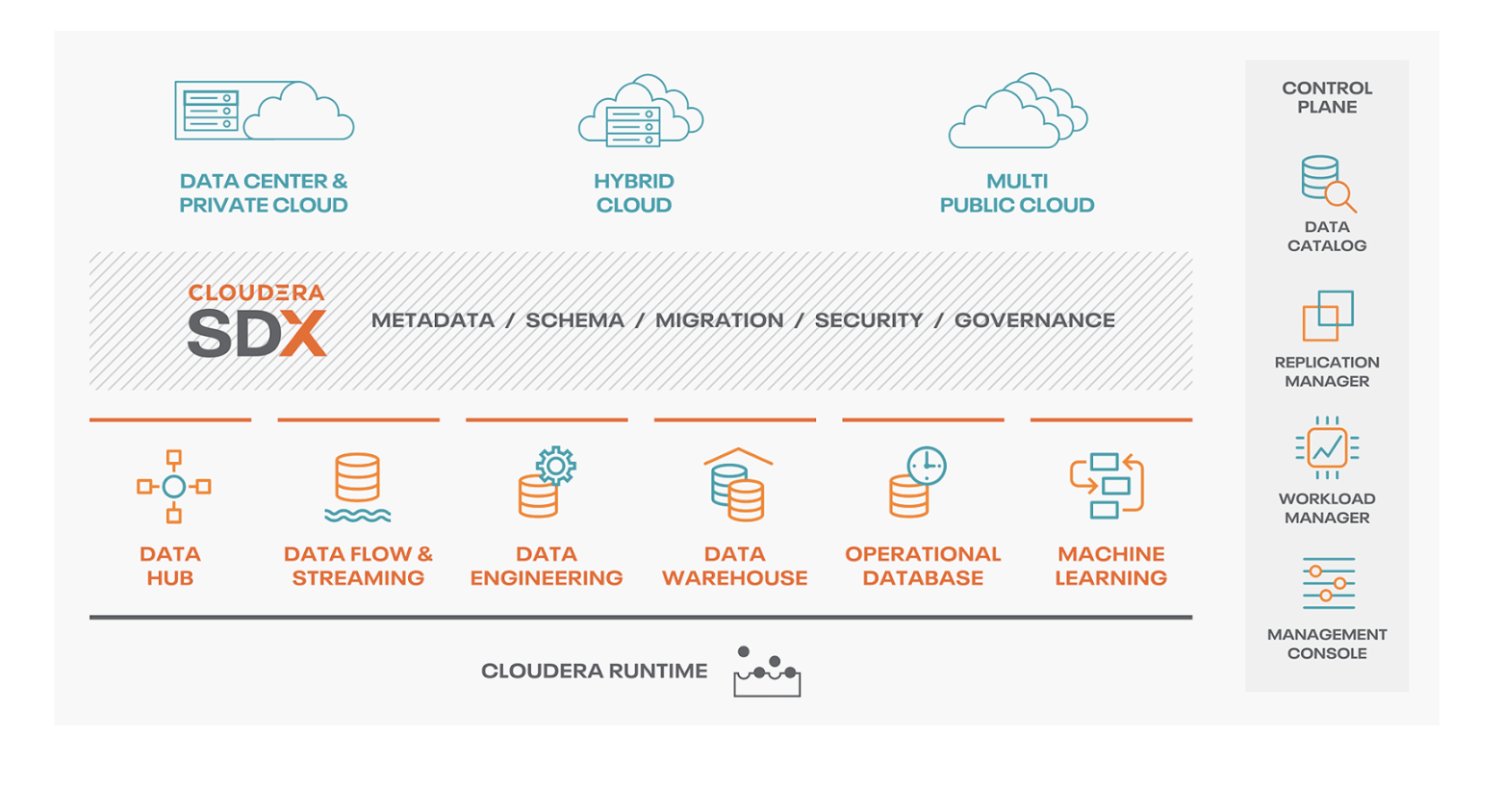
Cloudera Data Platform
The Cloudera Data Platform (CDP) is the foundation of the next-gen financial crimes platform and is represented in the blue base layer of my “Mind the Gap” diagram earlier. This enterprise data platform is what supports shared analytics and collaboration across specialized financial crime units and businesses, thus transcending the silos.
It also enables the unification of best of breed vendor solutions for fraud prevention, anti-money laundering, cybersecurity, and surveillance. This is because each can be plugged into CDP and iteratively enhanced with internal data science and machine learning initiatives and/or integrated with unique crime detection and prevention capabilities provided by cutting edge fin-tech firms.
CDP is built to enable a hybrid architecture (on-prem and cloud) with support for multi-cloud environments. With that in mind, data ingested from the edge with real-time streaming, embedded analytics, alerts, and dynamic transaction scoring can be aggregated and analyzed at a larger scale. Industrialization of machine learning and artificial intelligence support dynamic model updating and monitoring of that data so that enhancements can be sent back to the edge (i.e.: better-embedded analytics, alerts, and dynamic transaction scoring).
With CDP as the foundation, intelligence gaps are mitigated by a holistic enterprise view of all customer and financial crime-related data (holistic KYC), systems, models and processes. You will also be able to tighten the loop between detecting and responding to new fraud patterns. CDP also supports open-source advances to ensure that your teams are able to experiment with and adopt the latest technologies and methods, which helps to mitigate technology and vendor lock-in. The diagram below illustrates the Cloudera Data Platform and its various components for enterprise management.
Conclusion
An effective response to combating financial crime goes beyond deploying best of breed platforms that specialize in distinct types of crime. Each is designed to solve specific problems but space in-between the resultant silos is where many criminal opportunities lie. It also results in intelligence gaps that thwart effective collaboration across internal teams, global institutions, and cross-jurisdictional regulatory and enforcement agencies.
The next-gen financial crimes platform, in this case, built on the Cloudera Data Platform will enable the best of breed applications, analysts, business, and data scientists to coalesce around a common data experience. With an enterprise paradigm such as this, you will be able to enhance current investments with the latest machine learning and advanced analytical methods to unearth behavioral dimensions that are needed to proactively disrupt crime and mitigate risk, rather than just reacting to it.
For More Information
- Register for our upcoming webinar: Moving Towards the NextGen Financial Crimes Platform
- Download the eBook – Fighting Financial Crime: Top 5 Data and Analytics Approaches




Great post Paul. The current methods to fight cyber-crime are manual and disparate. We need to start using the same tools to protect as the criminals use to attack