By now, almost everyone across the tech landscape has heard of the Zero Trust (ZT) security model, which assumes that every device, application, or user attempting to access a network is not to be trusted (see NIST definitions below). But as models go, the idea is easier than the execution.
To provide guidance to federal agencies, and in many ways lead the way for the private sector, the Cybersecurity and Infrastructure Security Agency (CISA) issued the initial Zero Trust Maturity Model (ZTMM) in 2021 with the intent to give agencies a conceptual roadmap to onboard to a shared zero-trust maturity model by 2024. Subsequent to the ZTMM release, CISA issued a request for comment, which has led to the revised version 2 of the ZTMM in April 2023, as “commenters requested additional guidance and space to evolve along the maturity model,” according to CISA.
The revised ZTMM is organized by five categories or pillars: identity, devices, networks, applications and workloads, and data, and four levels of maturity: traditional, initial, advanced, and optimal.
Focusing on the Data Pillar
According to the Federal Data Strategy, the federal government views itself as the “preeminent supplier and sophisticated and ethical user of data.” With use cases from citizen services to military intelligence, government data is leveraged as a strategic asset across agencies (civilian and DoD). Moving to the “optimal” stage of maturity is critical to eliminating unauthorized access by bad actors, both foreign and domestic.
To reach optimal maturity, the ZTMM summarizes, “Agency data should be protected on devices, in applications, and on networks in accordance with federal requirements. Agencies should inventory, categorize, and label data; protect data at rest and in transit; and deploy mechanisms to detect and stop data exfiltration. Agencies should carefully craft and review data governance policies to ensure all data lifecycle security aspects are appropriately enforced across the enterprise.”
How does Cloudera support the evolution to optimal?
Zero trust as a principal is key to enhancing your security posture, but zero trust with proper governance frees the data so you can share it effectively within the organization. It’s a win-win. The data is protected but it is also accessible by the people who need it. This is the balancing act of security.
Cloudera Shared Data Experience (SDX) is a core component of Cloudera Data Platform’s architecture. It operates independently from compute and storage layers, offering integrated security and governance based on metadata. With persistent context across analytics and cloud environments, SDX simplifies data delivery and access with a unified multi-tenant model. This reduces risks and operational costs while enabling faster deployment of secure and governed data lakes for broader data access.
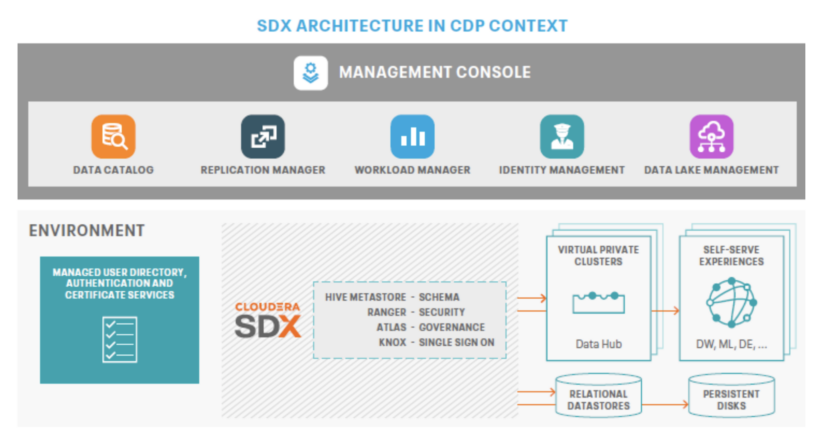
Cloudera adheres to the guiding principles of a Zero Trust Architecture as follows:
Verify Explicitly
Cloudera offers multi-factor authentication everywhere, providing a normalized SSO token for representing the authenticated user. This token is generally used for WebSSO capabilities for end-user consumption of the REST APIs available in Cloudera’s software.
Use Least Privileged Access
Cloudera leverages Ranger to limit user access using both RBAC and ABAC policies. With Ranger, administrators can create default policies that deny access to all resources managed by Cloudera. Individual users and groups of users can incrementally be granted access on an as-needed basis. Permissions are fine-grain and can be configured using time-based windows.
Data Protection
Cloudera leverages Navigator Key Trustee Server and Ranger Key Management Service to create zones of resources that are encrypted using unique and strong-cipher keys. Users and groups of users granted privileged access to a resource must also be given access to the appropriate zone key to decrypt the underlying data. This minimizes the blast radius of a breach through segmented data access.
Cloudera also leverages strong-ciphered TLS to encrypt all data-in-motion. This includes information exchange between Cloudera services and all end-client connections.
Auditing
Cloudera provides complete auditing of all resource access and user behaviors through Ranger’s centralized auditing tooling. The user and resource audits can be forwarded to a SEIM solution for proactive monitoring and alerting.
Additionally, Cloudera satisfies sections six, seven, and eight of the Executive Order on Improving the Nation’s Cybersecurity with real-time collection and scalable analytics of log data. Long-term retention of logs and robust machine learning capabilities gives agencies a powerful tool for threat hunting, investigation, and remediation.
Governance and data cataloging
Cloudera prioritizes governance and cataloging through governance tools Apache Atlas and Data Catalog. With Apache Atlas, Cloudera enables governance controls that effectively address enterprise-scale compliance requirements. Data Catalog helps the organization understand its data by building metadata and simplifying the creation and maintenance of Ranger policies. Understanding your data is critical to protecting the data.
Learn more about Cloudera’s approach to security and compliance at cloudera.com/trustcenter.



