Cloudera Data Platform (CDP) Public Cloud allows users to deploy analytic workloads into their cloud accounts. These workloads cover the entire data lifecycle and are managed from a central multi-cloud Cloudera Control Plane.
CDP provides the flexibility to deploy these resources into public or private subnets. Nearly unanimously, we’ve seen customers deploy their workloads to private subnets. It is the most secure deployment option, but this prevents direct access to their resources from the public internet and makes it difficult for their users to access the UIs and APIs in SDX and DataHub clusters. To give users access to these resources, customers have to set up complex custom networking such as custom proxy servers or point-to-point networking solutions like VPN Gateways, Direct Connect etc.
Point-to-point solutions can be expensive to provision and take multiple days of coordination with numerous IT, network, and cloud operations teams to implement. This can be onerous for customers who want to do a POC in an isolated VPC not connected to corporate networks. In addition, our current highly distributed work environment has made these point-to-point solutions, which worked great when we were all in one office, a less attractive alternative.
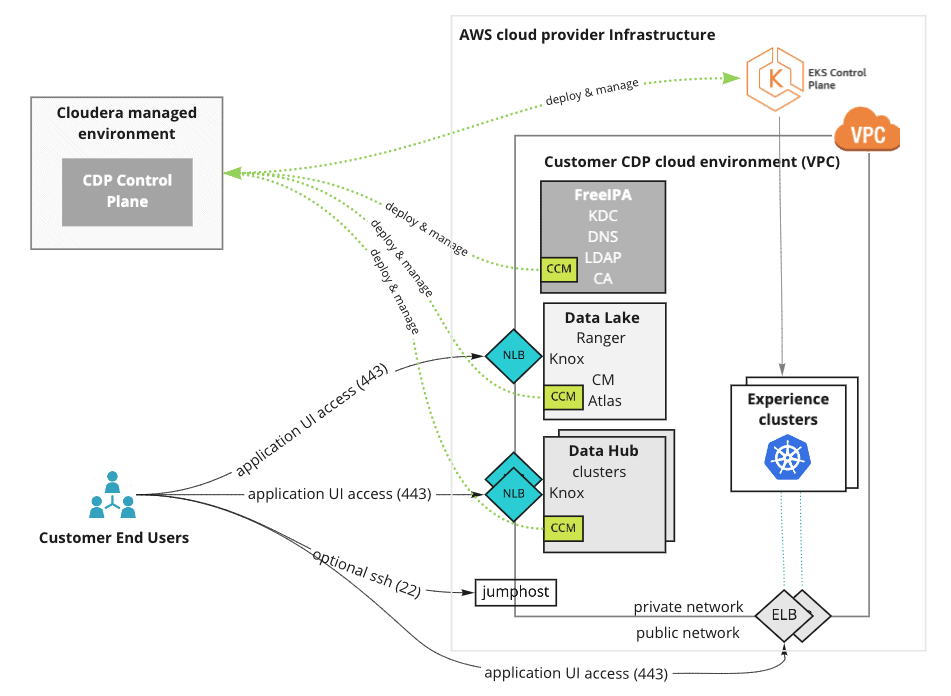
Today, Cloudera has launched the CDP Endpoint Access Gateway. At the heart of the solution is an internet-facing Load Balancer provisioned in the customer’s network that provides connectivity to CDP resources. This allows customers to access the UIs and APIs of CDP resources without the need to set up complex networking solutions.
CDP Endpoint Access Gateway
The gateway interfaces the Knox service, which is automatically integrated with the identity provider configured in CDP, allowing you to authenticate using your SSO credentials without any additional configuration All communication with the Endpoint Access Gateway is over TLS, so connections are secure. CDP can also be configured with Security Group settings to restrict public access to limited IP ranges by configuring IP CIDRs in the default security group configuration.
The Endpoint Access Gateway is optional, and must be enabled when creating a CDP Environment. There is no additional charge for the Endpoint Gateway; you only pay for the cloud resources used to support the gateway.
When enabled, it provides a secure connection between end-users on a public network and workloads running inside their private network. Customers can use the Endpoint Gateway to easily access the Ranger and Atlas UIs of their SDX clusters and all of the UIs and APIs in their DataHub clusters.
All Knox-enabled endpoints are supported. The gateway does not cover SSH or data access paths (such as Kafka Broker and NiFi Site2Site endpoints). We recommend that you set up connectivity between private networks in the public cloud and internal networks for secure and performant Kafka and NiFi deployments.
With the CDP Endpoint Access Gateway you now have flexibility to deploy workloads in a variety of network configurations based on your use case and the need for line of sight into your clusters. CDP now supports deployment into public subnets, private subnets with VPN/Direct Connect/Peering, or private subnets with Endpoint Access Gateway.
The CDP Endpoint Gateway is currently available for AWS; support for other clouds will follow shortly.
For more details, please read the documentation and sign up for hands-on experience with the platform with a no cost Test Drive at https://cloudera.com/testdrive



